Secure Android Devices: Top 10 Tips & Tricks for better Privacy & Security
Secure Android devices with these 10 simple tricks. Advertisement Over the years, Android has become more secure platform because of the efforts put in by the developers. When we say “secure Android”, […]
Secure Android devices with these 10 simple tricks.
Advertisement
Over the years, Android has become more secure platform because of the efforts put in by the developers. When we say “secure Android”, it simply isn’t limited to setting a phone lock, like a PIN or password. But, taking effective measures that would ensure that your personal data is protected and completely under your control.

Just think of the amount of data you have on your device. Your emails, important notes, personal contacts, messages, none of it that you would like to share anonymously. But things may slip down your hands if you don’t start caring for them right now.
Advertisement
While OEM offers several methods to protect your data, there are a few techniques that are common to all Android devices, irrespective of the manufacturer. We are going to lay down these techniques in the form of steps, which will help you take a step forward towards your Android’s privacy and security.
Page Contents
- Tips and Tricks to secure Android Devices
- 2. Manage App Permissions
- 3. Take A Backup More Often
- 4. Install Apps, Not Malware
- 5. Secure Your Device Using Android Device Manager
- 6. Preserve Privacy By Creating Multiple User Accounts
- 7. Encrypt Your Data
- 8. Do Not Save All Your Passwords
- 9. Use A Secure Messaging App
- 10. Think, Do You Really Need Root?
Tips and Tricks to secure Android Devices
1. Set A Password First
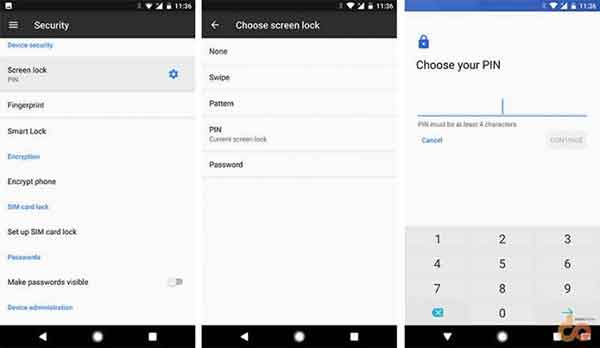
Just setting a lock on your phone is the simplest, easiest, and the most convenient way available to secure Android devices. All these years, Android evolved with not just better features, but also a more secure platform. The list of available screen lock methods has also increased over this period.
Since last year, we have seen fingerprint unlock which is adds an extra level of security to the lockscreen. Now it is available on a wide range of devices and is a much easier method to lock down your device.
To set up a lock on your Android, go to Settings > Security. On the very top, you will see “Screen Lock”, just tap on it. The available lock methods will be shown right there for you to select. You can choose from a pattern, PIN, or a complex password, whatever suits you.
2. Manage App Permissions
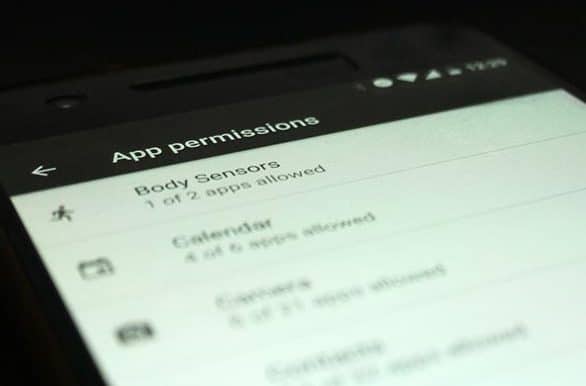
We all install apps daily, they are fun and innovative. But these apps are also the weakest link between the hackers and your private data. A lot of these apps require permissions to access services like Contacts, Telephone, Storage, etc. While most apps assure that your data would be only used anonymously for providing a better experience, there are chances that you might land on the wrong foot. If you ever get suspicious, you can simply deny the selective permissions.
Earlier, users would need to make use of third-party apps to manage permissions. With Marshmallow, users were given complete control on permissions that were given to the installed apps, which was a huge step; allowing the users to selectively permit each app.
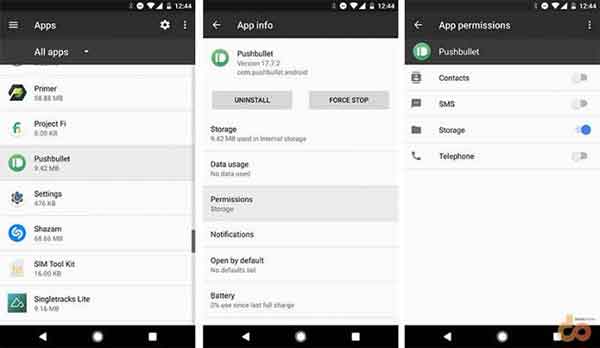
To manage permissions for installed apps collectively, go to the Settings > Apps. Tap on the Gear icon on the top-right and select App permissions. You can also manage per-app permissions by going to Settings > Apps > “name-of-the-app” > Permissions.
3. Take A Backup More Often
Don’t just backup your phone when you HAVE TO. Taking a regular backup of all your data could save you from a lot of trouble if you ever lose your Android.
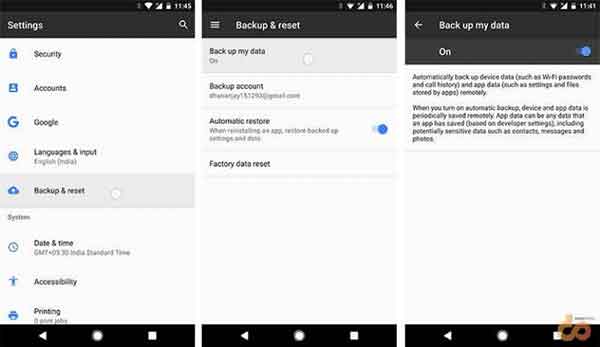
Google offers an in-house backup capability to backup the app data, call logs and WiFi passwords. To start off, go to Settings > Backup & reset > Backup my data and turn it ON.
Advertisement
For contacts, it is always better to sync them to your Google Account. This will take out any need to manually back up them. All your contacts will be available online through your Google account and synced across all your devices.
Google Photos is a huge savior when it comes to backing up your photos and videos to the cloud. It can automatically sync the latest media and also provide you the freedom to delete them from your device’s offline storage, thus saving space.
Manually taking a complete backup of your phone’s storage is a wise practice for added comfort. Just connect your device to the PC using USB cable, and copy and paste all the files and folders that you need.
4. Install Apps, Not Malware
Installing apps manually or from third-party sources could be harmful. The fact that some apps are not available at the Play Store, is because they do not comply with the policies laid down by Google. Which makes us question their integrity. So do not go freely installing apps from other sites until you are certain that they are not modified in any manner.
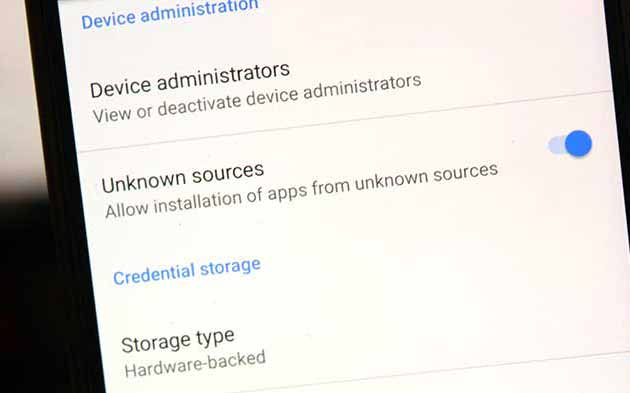
There could be apps that are not available in your county or a specific update hasn’t reached you yet. In such situation, if you are really looking for a secure and reliable source for Android APK files, you can download them from APKMirror.com. It ensures that the cryptographic signature of the uploaded APKs match that of the original ones at the Play Store.
Please note that APKMirror follows a no-piracy policy and so it does not host any paid apps. We encourage the same, so if you want a paid app, kindly pay for it. You will not only get premium features, but also support the developer for his hard work.
5. Secure Your Device Using Android Device Manager
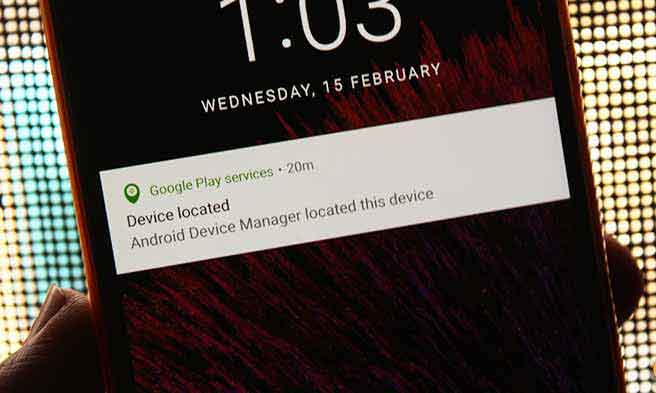
Losing your precious Android is the most devastating thing that could happen. You may have forgotten it over a few beers or someone may have stolen it. In either case, you can use your device’s GPS and Android Device Manager to relocate your lost Android device. There are several tracking apps available out there, but we trust Google’s own Android Device Manager to be more reliable and easy to operate.
Note that in order to locate your device, the location and data services should be turned ON. If either of those is OFF, there is no way that ADM or any other similar app would be able to help you.
First, you need to set up your Android. Go to Settings > Google > Security. Enable “Remotely locate this device” and “Allow remote lock and erase” options.
Advertisement
Go to the Android Find My Device page on your desktop browser and sign-in with the same Google account that is registered on your lost Android device. Or, If you have another device with the same account, just install ADM from Play Store and open the app. You shall have your device location displayed on the screen.
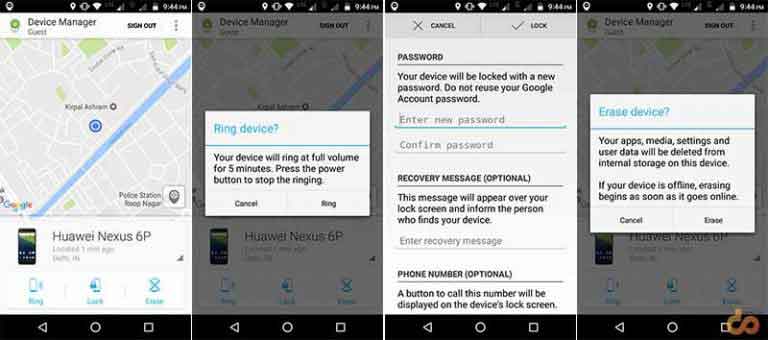
ADM not only relocates your lost device but also helps you take some effective measures to secure it.
- Ring: The option allows you to ring your device at the highest volume constantly for 5 minutes.
- Lock: If you believe your phone is stolen, then this is the first step that you should take instantly after relocating it. You can add a new password, along with a message and your contact number to leave on the lock screen. Using some bribe in the message would be wise idea. For example, type − “Hi this is Josh, this phone’s owner. If you have found it, kindly call me and I shall award you with a decent amount of money or a treat”. This sort of message will tempt the founder and increase the chances of you getting your phone back.
- Erase: If applying a lock and a message doesn’t work. The last resort would be to erase your device completely. This will prevent any personal data to be exposed or misused.
6. Preserve Privacy By Creating Multiple User Accounts
Let’s say you are handing your phone over to a colleague, your kid, or an unknown person. In such situations, creating separate user accounts will help you preserve your data and privacy. A different user profile can have its own personal Google account, along with the space to install apps, games, and what not.

If you are using an Android smartphone or tablet with Android Jellybean or up, you can set up multiple users on it. Just head over to Settings > Users and tap on “Add user” or simply drag down the Quick Settings and tap on your user profile icon.
7. Encrypt Your Data
Encrypting your device and all its data can take your phone’s security to the next level. What it does is, convert all your data to a complex and scrambled code. The data then could not be accessed until it is decrypted using a secure key.
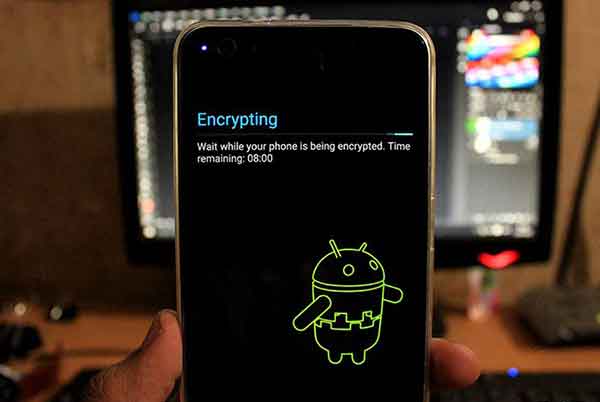
While most Android devices now come with auto-encryption, there are unofficial ways to remove it. But we advise you to have your device encrypted at all times. This will create a strong wall between your data and any outsider that may try to access it.
Go to Settings > Security > Encrypt phone to start encrypting your data. When your device is encrypted, every time you turn on your device, you will be asked for the set password. Failing to do so will leave the data redundant, so make sure you set something that you can remember, and at the same time, it is difficult enough for someone to figure out.
Advertisement
To know more about encryption, click the link below.
— How to encrypt Android Smartphones and Tablets
8. Do Not Save All Your Passwords
While saving passwords is more convenient and easy, it could serve as a potential weakness to your accounts that could be accessed with those passwords. A person who can access your phone will then have the power to misuse your accounts. The straight solution is to not save passwords for your important accounts, whether in Chrome, Opera, or any other browser.
If you still want to save them, you can do it with a rather secure app like 1Password. The app is a simple yet very affective password manager and wallet. It is well secured and trusted by over thousands of users.
Download 1Password from Google Play Store
9. Use A Secure Messaging App
Messaging is the next-generation way to exchange information, other than emails. It is fast, but then could also be the easiest one to hack into. Higher authorities like the government could dig out your data within seconds and grab your shared information without much hassle.
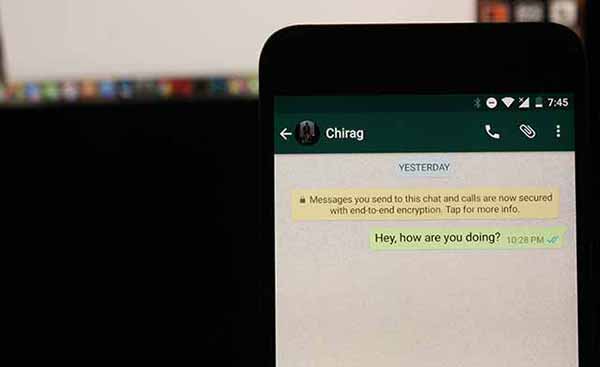
To deal with this, messaging apps have started to implement end-to-end encryption method. It locks down all your messages that you send to a recipient and only him and you will have the key to unlock those messages. The lock and key are generated automatically and no extra effort is required. Instant messaging apps like WhatsApp and Telegram have already administered end-to-end encryption. This will ensure that all the data that you share is secure and could not be read by anyone else.
If you’re using a messaging app that does not offer this technology, then we suggest you switch as fast as possible. You can download one of the following apps and feel more secure while getting in touch with people you love.
10. Think, Do You Really Need Root?
Rooting opens up the gate to endless modifications and tweaking, but it also creates a backdoor for hackers to sneak into. Allowing an app root permissions is risky, especially when you are fiddling around with them. A root-requiring app from an unknown source could risk your device’s security as well as your personal data to a great extent.
Have you rooted because the guy next to you has done it too? Just think of it, are you really making use of any apps or mods that require root permissions. If the answer is no, unroot your device right away and stay away from Root, unless you really need it. It will give you a better sense of security.
These were our 10 tips and tricks to secure Android smartphones and tablets. Most of these tips and tricks are something that we put to use on all our devices, and you should too. Overlooking the risk of data theft is not a good thing, so do something before it is too late.
Share this article on your social media and help your friends get the most out of their Android’s Security & Privacy
Some more interesting stuff for you: