How to Detect Procfs Android System Vulnerability and Fix it (Root)
Today, we are here to make you aware of a recently-discovered Android System Vulnerability. Magisk developer @topjohnwu, who discovered it, has also released an app called “ProcGate“. The app will help you […]
Today, we are here to make you aware of a recently-discovered Android System Vulnerability. Magisk developer @topjohnwu, who discovered it, has also released an app called “ProcGate“. The app will help you detect the Procfs Android System Vulnerability on your device. If your phone is rooted, then the app will also help you fix the vulnerability.
Advertisement
The Magisk developer wrote a post on Medium.com, explaining the whole situation that led him to discover this system vulnerability. Following which, folks at XDA-Developers posted a detailed article, talking about the same. Instead of repeating the whole scenario over here at our blog, we decided to highlight the major parts of it, and especially how an end-user can detect Procfs Android System Vulnerability on his device and fix it (Only if the phone is rooted).
Along with the nifty article, topjohnwu also released “ProcGate”. It is an app that can help rooted users easily detect and fix Procfs vulnerability on their phones.
Page Contents
Brief: Procfs Android System Vulnerability
Well, instead of making long paragraphs about the said vulnerability and repeating the information, I decided to put down the major part of the information in a brief format. However, if you’d still like to dive into the details, I suggest you take a walk through the posts linked above.
Advertisement
- topjohnwu explored a popular Anime gaming app (Fate/Grand Order) for its root detecting mechanism.
- Upon days of testing and exploration, the developer found that the said app exploits a bug to detect root on a device.
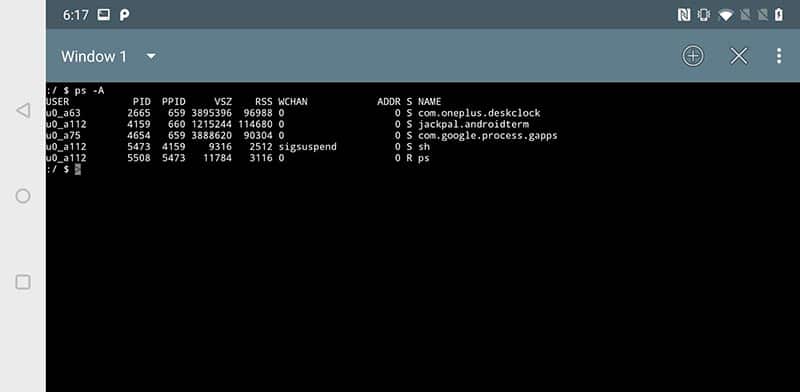
- The bug: Being able to mount
/procfswithout thehidepid=2flag - Any app that can do so, can read the process information, status, and mount points of other apps.
- FGO uses this to detect MagiskHide and thus prevents users from playing.
- All Google (Nexus/Pixel) and a majority of Samsung devices implement proper security feature. So these are NOT vulnerable.
- The developer used a OnePlus 6 running OxygenOS 9.0.2 (Android Pie) and it is exposed to the Procfs Android system vulnerability.
- OEM devices from Asus, Honor/Huawei, LG, Xiaomi, etc are vulnerable. Check the list below.
- The vulnerability could be patched through a system upgrade or by remounting
/procusing proper flags with root permission.
Devices Affected with Procfs Vulnerability
XDA developers have already posted a list of various popular OEM devices that are affected with procfs Android system vulnerability.
Since it is not possible for them, or for us to test all the OEM devices, it would be nice if you (the users) can test and report (Check the section below) if your specific device is vulnerable or not.
[table id=13 /]
If your phone is not listed above, we request you spare a few minutes of your time and use the ProcGate app to detect the vulnerability on your device.
How to Detect and Fix Procfs Android System Vulnerability?
The detection part of ProcGate will work on any device, rooted or not rooted. However, if you’d like to fix the vulnerability using the app, then your phone must be rooted (Magisk is the way!). Now simply follow the steps below.
- Download ProcGate APK file on your Android device:
- Open a file manager app of your choice.
- Navigate to the folder where the APK was downloaded.
- Tap on “ProcGate.apk” and follow the on-screen instructions to install the app.
- Once installed, go to the phone’s app drawer and launch ProcGate.
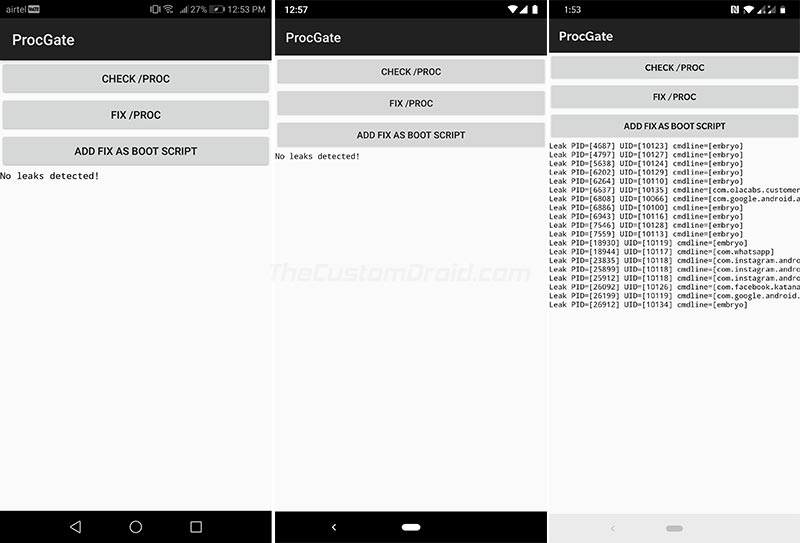
- Tap on “CHECK /PROC” to detect procfs Android system vulnerability on your phone.
- If there are no proc leaks, then you shall see the “No leaks detected” message.
- If any process leaks are detected, then you can tap the “FIX /PROC” button to properly mount
/procwithhidepid=2flag and fix the vulnerability.
I have already tried the app on Honor 9 Lite (Android 8.0 Oreo), Pixel 2 XL (Android 9 Pie) and OnePlus 6T (Android 9 Pie), and the results could be seen in the screenshots below.
Should You Be Worried?
Procfs Android system vulnerability is not as severe as some of the previously known vulnerabilities like Blueborne, KRACK, etc. Even if your device is vulnerable, there’s no chance for an app to analyze your personal data.
For security concerns, no app should be able to mount /proc without hidepid=2 flag. Google has already pushed a patch to Android CTS (Compatibility Test Suite) to ensure this. As for the rest of the Android OEMs, they should implement this too. According to XDA, OnePlus is already aware of the vulnerability and is working on a fix.
We would like to thank Magisk developer topjohnwu for finding this flaw and XDA-Developers for working along with him to test the vulnerability on various devices.